Happy International Woman’s Day.
Firewall is the barrier between a trusted and untrusted network. Before diving into statefull firewall. I wanna address what is a stateless firewall. This is when each packet is treated individually and we dont keep track of packets we have seen before or not.
In another word, that we need to permit or deny the packet using ACL by checking their layer3 and layer 4 header.
Okay, let me give you a small example of stateful firewall. A computer on the LAN uses its email client to a mail server to the Internet. The client will start from a TCP three-way handshake, with a TCP stateful table. And when we receive the SYN_ACK packet and we check the table to see if it is a legit packet.
Better solution with security zone.
Traffic from a “high” security level to a “lower” security level is permitted.
Traffic from a “low” security level to a “higher” security level is denied.
If we want to make an exception, we can always permit traffic from WAN to LAN with an access-list.
Most companies will have one or more servers that should be reachable from the Internet. Perhaps a mail or web server. Instead of placing these on the INSIDE, we use a third zone called the DMZ (Demilitarized Zone). Take a look at the picture below:
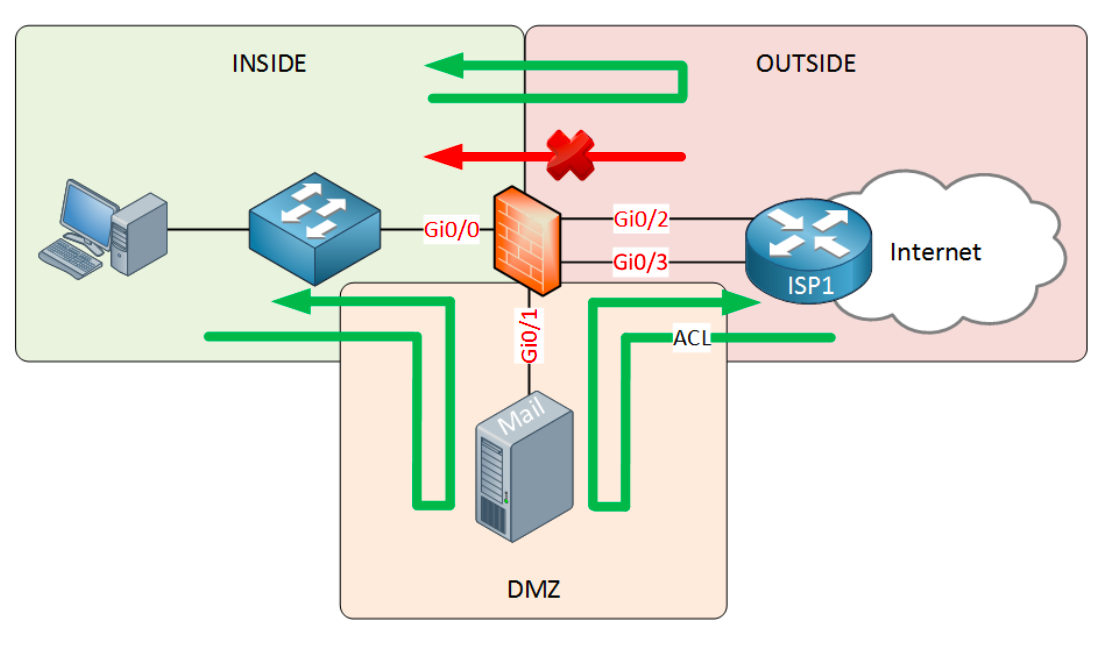 The DMZ security zone will have a security level that is between INSIDE AND OUTSIDE.
The DMZ security zone will have a security level that is between INSIDE AND OUTSIDE.
Let us jump into Ipsec VPN. link
This vpn tunnel is used to allow the secure transmission of data between two-sites. The vpn tunnel is built over the public network and encrypted using a number of advanced encryption algorithms.
ISAKMP Phase 1:
R1(config)# crypto isakmp policy 1
R1(config-isakmp)# encr 3des #encryption
R1(config-isakmp)# hash md5 #hashing algorithm
R1(config-isakmp)# authentication pre-share #pre-shared key
R1(config-isakmp)# group 2 #diffie-hellman group number
R1(config-isakmp)# lifetime 86400
NEXT, we need to define a pre-shared key for authentication with our peer using the following command
crypto isakmp key firewallcx address 1.1.1.2 #so we know neighbor ip public add
Phase 2: Configure IPsec We are going to create extended ACL, IPsec Transform, Crypto Map, Apply Crypto Map to the public interface.
- STEP 1: CREATING EXTENDED ACL
R1(config)# ip access-list extended VPN-TRAFFIC R1(config-ext-nacl)# permit ip 10.10.10.0 0.0.0.255 20.20.20.0 0.0.0.255 - STEP 2: ISAKMP PHASE 2
R1(config)# crypto ipsec transform-set TS esp-3des esp-md5-hmac - STEP 3: CYPTO MAP
This is to connect the previously defined ISAKMP and IPSec configuration together.
R1(config)# crypto map CMAP 10 ipsec-isakmp R1(config-crypto-map)# set peer 1.1.1.2 R1(config-crypto-map)# set transform-set TS R1(config-crypto-map)# match address VPN-TRAFFICLast step is just to apply the map into the interface.
There is possibilty that we use NAT to provide internet access to internal host.
When I am reading article about this, I accidentally saw the article about BGP roubleshooting. How do we deal with Idle OR route flap.
Double check if the tcp seesion is on cuz BGP is rely on that. Interface is up and ip address is configured properly. No authentication mismatch or firewall blocking stuff. No pointing to the wrong neighbor.